Recently there has been a number of successful cyber attacks against many different organizations’ cloud services. However, there are many security measures you can apply to defend your cloud solutions. If you use a defense in depth approach, you can build multiple layers of defense and reduce the risk of getting your valuable data stolen.

Defense in depth is a concept created by the US military to describe the placement of defensive barriers to impede the advancement of combatants from overtaking a held position.
This strategy included monitoring the combatants` progress and responding to their advances with equal or greater force.
The same concept is applied to the cyber security world. Threat actors are the combatants and countermeasures are the defensive barriers or layers. This is the foundation of the defense in depth concept.
Each layer is designed to prevent and delay one type of attack. The layers work together, so that if one layer fails to stop an attack, another layer takes over.
Even if an attack cannot be effectively prevented, it can be delayed, and detection of malicious behavior is more likely to succeed.
An analogy is a castle with multiple walls to stop attacks from adversaries.
Defense in depth overview
Traditionally defense in depth has been based on the 7 layers of the OSI model. These are: physical, data link, network, transport, session, presentation and application layer. This will not work for cloud security.
- Defense in depth is based on layers of defense
- Architectural layers is often used to design protective measures
- Layers can be combined with NIST Cybersecurity Framework (NIST CSF)
- The shared responsibility model for cloud must be considered

In this article, I will show you how to build a defense in depth strategy on architectural layers for the cloud. Each of these layers will also apply to each of the NIST CSF functions.
We will build a 2-dimensional defense in depth matrix that will be designed to cover all important aspects of cloud security and the 5 NIST CSF functions
This will help us visualize our cloud security posture so that we can identify in what areas we need to add more security measures.
In addition to the 2-dimensional defense in depth matrix we also need to identify responsibility. We need to identify our responsibility as cloud customers for the security measures and what the Cloud Service Provider (CSP) will be responsible for.
It’s a common mistake to believe that some areas of security are the CSPs sole responsibility. In reality, most security areas will be either shared or left to the cloud customer to fulfill.
Cloud shared responsibility
Cloud Service Customer (CSC)
The cloud service customer is responsible for security in the cloud.
Typical responsibilities are, depending on the service model, virtual network, virtual machines, operating systems, middleware, applications, interfaces, and data.
Governance, policies, end-point security and training are also responsibilities of the CSC.

Cloud Service Provider (CSP)
The cloud service provider is responsible for security of the cloud.
The cloud service provider is responsible for protecting the infrastructure that runs all of the services offered in the cloud. The infrastructure is composed of the hardware, software, networking, and facilities that run the cloud services.

Defense in depth layers
Defend your cloud solutions against hackers using a layered approach customized for cloud services. These layers are our defense in depth layers for cloud. As you can see in the illustration below, these layers are part of your cloud security architecture.

GRC Management
Governance, Risk and Compliance is the overall management of the cloud security program ensuring we have the right security measures to lower the total risk.
The Cloud Center of Excellence (CCOE) has the responsibility for governance, risk and compliance and will also manage the development of security architecture for the cloud. The CCOE will manage cloud security personnel and capabilities for detection, response and recovery.
Identity and access
Identity and access management is important as a layer of defense in the cloud. We are moving from a world with perimeter defenses to a world where identity is the new perimeter. Strong identity and access management processes are vital for success in the cloud.
Cloud provider tools for identity and access management should be used to handle identities and access to assets effectively throughout the cloud environment.
Security ops& Infrastructure
Day-to-day operations of security measures to protect assets is important also in the cloud. The infrastructure must be monitored for intrusion attempts 24/7 using tools for automation.
SecaaS tools from your chosen cloud provider should be utilized to run your security operations in the cloud.
Endpoint
Endpoints are even more important when moving to the cloud. Protection of mobiles, laptops and tablets is important for protection of the assets in the cloud. The endpoints should be scanned for vulnerabilities, automatically patched and anti-virus software must be installed.
An emerging trend is to upload endpoint security logs to the cloud for aggregation and analysis.
Application
A secure development process is key also in the cloud. Security must be built into applications from the beginning along with privacy. Attacks against applications running in the cloud exploit vulnerabilities in applications to gain access to your assets.
Protections against attacks on the application layer can be mitigated using a Web Application Firewall.
Data
It is important to protect data both at rest and in transit. Encryption of traffic and data in cloud storage are good mitigations to protect data from many different types of attacks.
The cloud provider offers many mechanisms for encryption and key management.
Security architecture capabilities
I would like to introduce both capabilities and components that will help us improve our security posture in the cloud. The output of an information security architecture process is a set of requirements and capabilities that will fulfill the set of requirements.
The capabilities shown in this article are all security measures, but they represent the organizational security measures that are part of our Governance, Risk and compliance layer.
Risk management is a mandatory activity that will go on continuously and will be important for our cloud security architecture.
Cloud compliance is important both for the CSP and for you as a cloud customer. Even if the CSP can document compliance, its your responsibility to offer the same level of compliance for the services you design on top of the cloud infrastructure.
This applies to all service models, but particularly to IaaS and PaaS where you, as a customer, has many responsibilities for security.
Cloud governance represents the overall management for the cloud initiative. The CCOE performs cloud governance function managing personnel and resources assigned to work on cloud solutions.
The audit capability is important for ensuring that the cloud services stays compliant. For a cloud environment processing sensitive data, its vital that auditors verifies the cloud platform of choice and that the cloud customer environment is implemented in compliance with regulations.

Risk management
Risk management is a continuous activity and important for prioritizing resources

Governance
Cloud governance is important for managing cloud security initiatives

Compliance
Many organizations must prove compliance to regulatory requirements such as HIPAA for the healthcare sector

Audit
Both the cloud provider and the cloud customer must audit operations, governance and environments to improve and stay compliant
Security architecture components

Anti Virus
Anti Virus software protects endpoints like laptops and mobile units against malware
Application security
Application security is about building secure applications by building security into the development process

Device security
Device security helps protecting endpoints against unauthorized access to data
Data protection
Data protection guards sensitive data against unauthorized access

Encryption
Encrypting data at rest protects against many types of attacks by keeping data confidential

Web Application
Firewall
A Web Application Firewall protects web applications against attacks from adversaries
Anti virus software is essential for protecting the users devices and will be leveraged to protect end users from malware.
A Web application firewall protects web applications. This is a very important component for protection at the application layer as most applications for cloud are build using web technologies.
Device security will be utilized to monitor and protect information used locally on end users devices from unauthorized access.
Databases need their own protection mechanisms. Databases in the cloud often have security features for protecting data against unauthorized access.
Application security is important for building secure applications. Scanning for vulnerabilities in code should be performed during the automated deployment process.
Data encryption is a very important security measure that can protect data against many types of attacks. Data can be encrypted independent of storage mechanisms in the cloud.
Security measures in layers
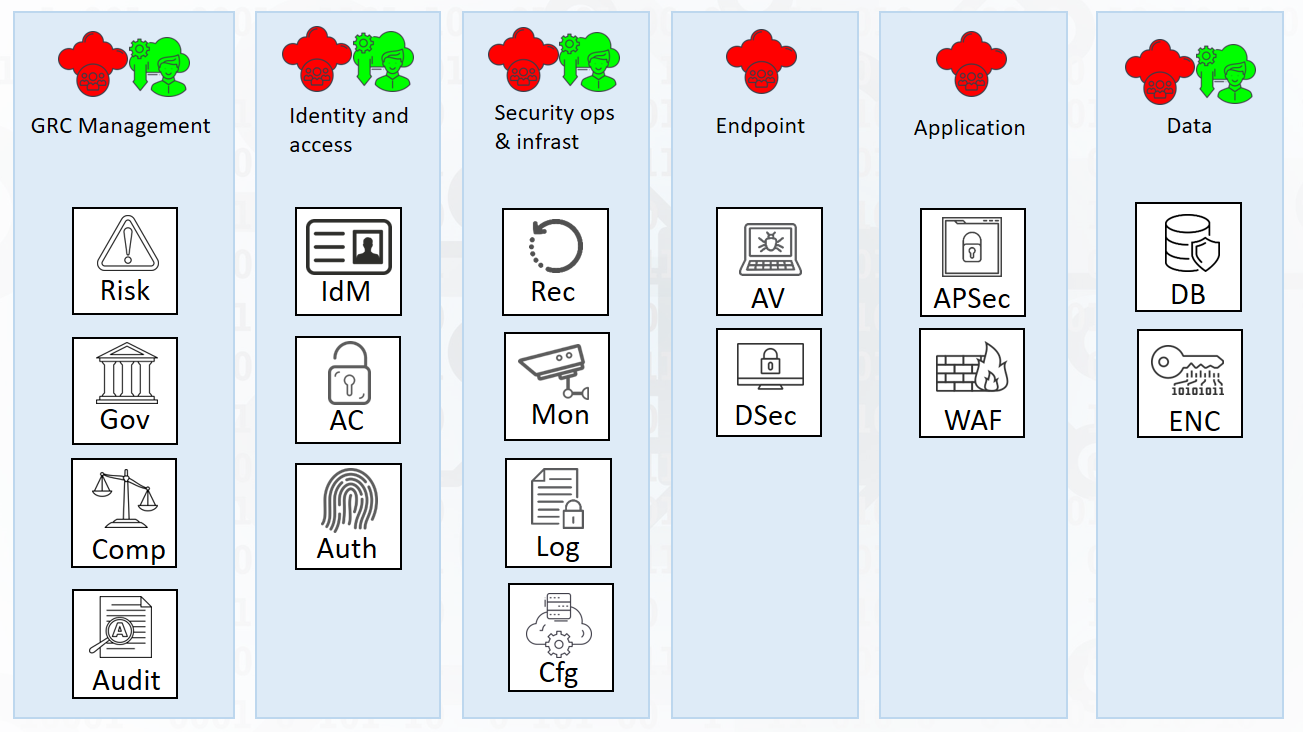
As shown in the illustration above, placing the security components and capabilities in layers will visualize how we can build our cloud security posture.
The components map to NIST CSF sub-categories. These components can be directly mapped to services in the cloud providers catalog.
Endpoint, Application and Data have only two components assigned for those architectural layers. This may seem a bit few.
But these components can be mapped to many different cloud security services depending on the cloud provider you choose.
For governance, risk and compliance, i have marked this layer as shared responsibility between cloud customer and the CSP. This is because audits of the cloud platform and fulfillment of service level agreements is the CSPs responsibility.
For Identity and access management, security operations and infrastructure the CSP also have a responsibilies. I addition to providing tools for Idenity and access management and security monitoring, the CSP will have infrastructure responsibility when the PaaS model is used.
Endpoint security and application security are the cloud customers responsibility. However, if you choos a SaaS delivery model, the application layer will be the CSPs responsibility.
Data security is a shared responsibility. The CSP has responsibility for physical storage media and data protection services. You, as a cloud customer, must use the protection services to protect your data.
Defense in depth matrix
When we list our security measures in the defense in depth matrix we can start seeing what type of coverage we can achieve across the NIST CSF functions.
For this example the cloud security architecture has 8 sample requirements.
Security requirements
S1 -Sufficient confidence in the actors’ identity and strong authentication
S2 – Access to information based on ownership or service needs
S3 – Traceability for all operations on PHI in the clinical platform
S4 – Granular role-based access control
S5 – Protection of sensitive data from unauthorized disclosure using encryption
S6 – High availability – according to the criticality of the solution
S7 – Change management adapted to cloud delivery
S8 – Business continuity and disaster recovery must be addressed in the solution infrastructure
The sample security requirements are mapped to NIST CSF sub-categories.
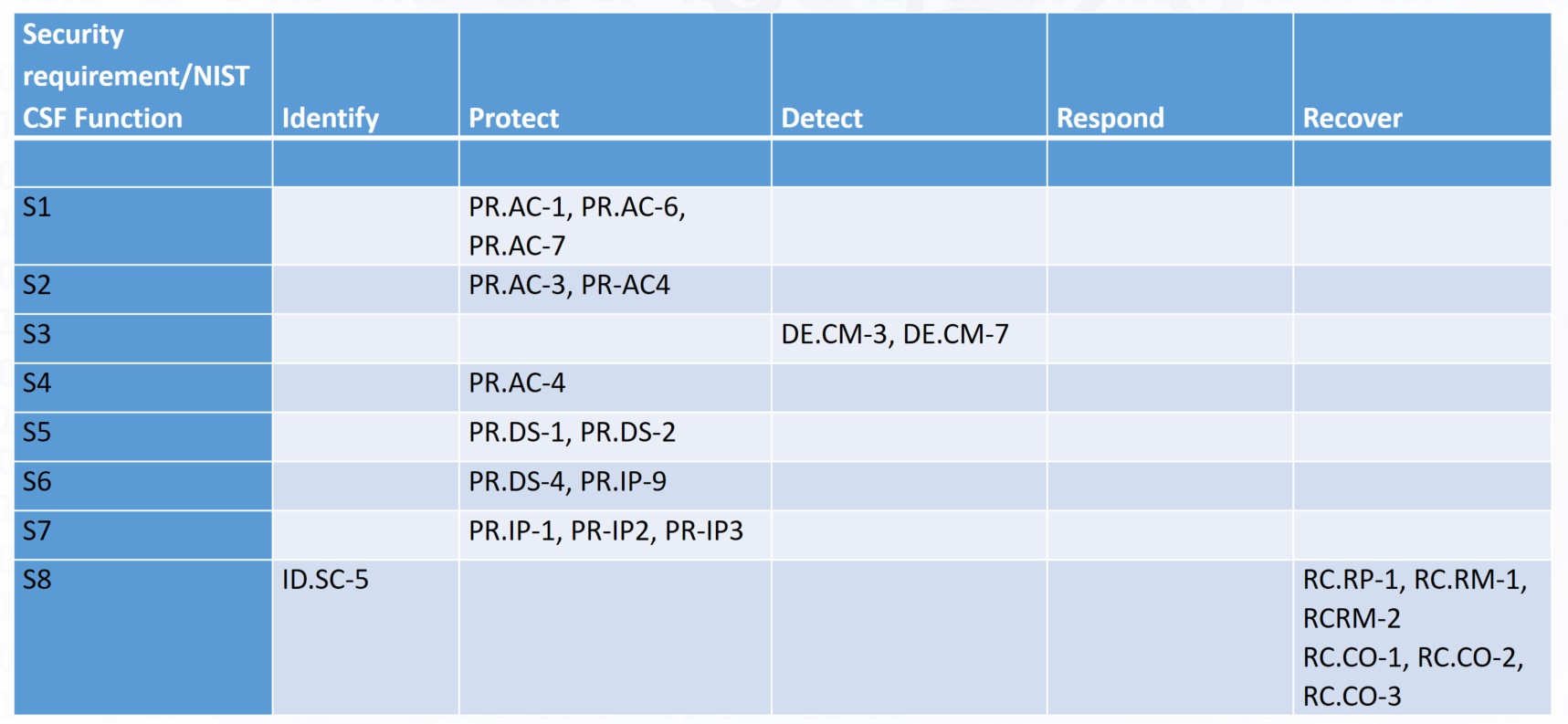
When we list our security measures in the defense in depth matrix we can start seeing what type of coverage we can achieve across the NIST CSF functions.
As you can clearly see most of the security measures are listed under column for the Protect function of NIST CSF. Some are listed in the Identify and Detect and the rest in Recover column.
The Respond column does not have have any measures yet. In a real situation, when we list many security requirements, all NIST CSF functions should be covered.
Anyway, security requirements mapped from business- and regulatory requirements will never give enough security requirements to build a resilient security posture for our cloud environment. Here is were the risk assessment comes in. It will provide us with many more mitigation measures.
The defense in depth circle
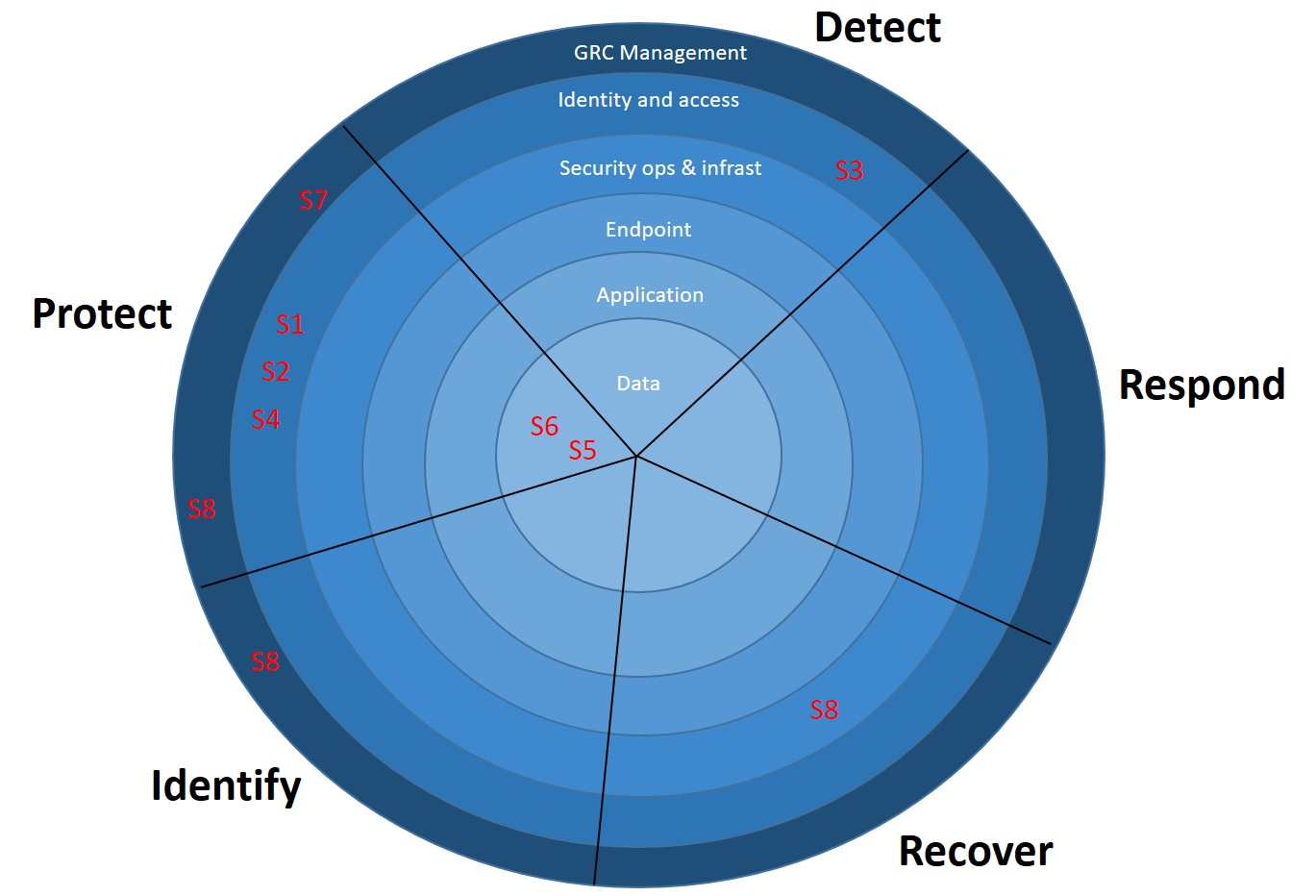
This is our Defense in depth circle. I think this looks more pretty that the matrix, but maybe that’s just me.
We have 5 sectors of the circle, each representing a NIST CSF function. We also have 6 circles representing each architectural layer.
The idea is to visualize the defense in depth coverage using this circle. The more circles that are filled with security measures in each sector, the better. However, the circle does not need to be completely full to represent a good security posture.
To make the visualization more readable we just add the security requirements. Adding the NIST CSF sub-categories would be too granular for this view.
The security requirements are all mapped to NIST CSF sub-categories. This makes it possible for us to decide where they belong in the circle. We will place them in the right architectural layer and sector according to what type of measures they are mapped to.
Visualizing the security measures in this way will make it clear what the cloud security posture looks like. This will form a basis for a cloud security initiative.
Defend your cloud solutions against hackers using the defense in depth approach described in this article!
You are a very bright individual!